Designing Secure Applications and Architectures
Designing Secure Applications and Architectures Free Tutorial Download
Description
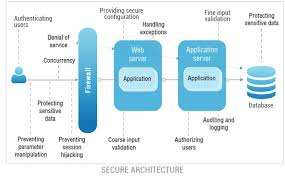
Domain Three – Specify Secure Application and Architectures – Introduction
Securing Applications and Architectures comprises 26% of the exam criteria and requires the following:
3.1 Determine how to secure application tiers.
3.2 Determine how to secure data.
3.3 Define the networking infrastructure for a single VPC application.
Transcript
Hello, I’m Stuart Scott, and I’ve created a number of the courses within this domain which focus on security. In the past two years, there have been numerous high profile security breaches which has ultimately resulted in the loss or exposure of millions of personal customer data records. The headlines provide a constant reminder of the disruptive impact this has on a business in the wake of one of these breaches.
Security today still remains a top priority for both AWS as a public cloud provider and for its customers who are using the services to secure their data and cloud solutions. Throughout this domain, we will look at security from a number of different perspectives to help you secure, manage, and protect your data and services. Firstly, let’s review the domain criteria.
This is split into three different sections which dictates that you must be able to determine how to secure application tiers, determine how to secure data, and define the networking infrastructure for a single VPC application. I shall begin by addressing a number of key services such as Amazon S3, Amazon Redshift, Amazon EMR, among others to explain how these services have their own methods of controlling encryption to ensure your data and application remains protected and secure at all times.
I will then talk about the Identity and Access Management service, which is critical to manage, control, and govern authentication, authorization, and access control mechanisms of identities to your resources within your AWS account. I shall discuss how through the use of users, groups, roles, policies, and access mechanisms you can create a secure and robust access control strategy to effectively and efficiently ensure your data is secure and safe from unnecessary exposure.
Diving deeper into access control, I shall also focus on the various different means of authentication and authorization mechanisms provided by AWS. I shall discuss how a combination of these can be used to set secure standards to your internal security policies. Preventing an identity of gaining access to a resource that they should not be permitted to access can prevent a large number of security vulnerabilities, and so it’s important to firstly understand the difference between authentication and authorization and then the methods of enforcing these within your environment. I shall also discuss the different security controls that are available to provide the best practice security across a range of services that fall outside of the infrastructure as a service security umbrella by focusing on services such as S3, which is an abstract service, and RDS, considered as a container service.
I’ll also look at segmenting your VPC and how this can also enhance your security profile. Diving deeper into the process of the encryption itself, you’ll also learn and understand how and when to use the Key Management Service known as KMS. This service is used to help you manage, generate, and control data access keys, allowing you to perform encryption of your data. KMS works with a large number of services, leveraging the potential of enforcing strong encryption controls when needed. There’ll also be a number of different labs in this domain, allowing you to get hands-on with a live AWS environment provided by a platform that will guide you step-by-step on how to configure specific security-centric tasks.
Download Designing Secure Applications and Architectures Free
https://mshares.co/file/vSlS1L8
https://jia666-my.sharepoint.com/:u:/g/personal/hoquangdai_xkx_me/EZSrjrhgYuhFpfPLIaHj2AoBZsMYBGGPTMwzQHC6w2q6yw
https://anonfile.com/Rd3383o4oa
https://drive.google.com/a/my.riohondo.edu/file/d/1PQQIOKFzT0ZVRN6y5PG58CVHftRGuktK/view?usp=sharing
https://uptobox.com/07dvgo3zxmxs